Threat actors are becoming increasingly sophisticated, with ever more powerful tools. Despite advancements in authentication methods, passwords continue to underpin the typical authentication workflow. Organizations that invest in protecting this critical aspect of the process see dividends in enhanced protection from ransomware, software compromises, and customer data theft that can cripple an organization.
Enzoic has sponsored this post. If you’d like to learn more about Enzoic for Active Directory, check them out!
Enzoic for Active Directory integrates with your existing Active Directory (AD) environment to provide much-enhanced user password protection. This ATA Learning product review looks at the effectiveness and ease of use of Enzoic for Active Directory.
Getting Started with Enzoic for Active Directory
As with most services, the first step is to sign up for an account, which grants access to the Enzoic Console. Enzoic offers a free tier for each product, which I appreciate as a great way to evaluate its offerings. Once basic details are entered, a “Getting Started” page is displayed. From there, you can schedule a meeting with an Enzoic representative to learn more or open product documentation.
I appreciate that there are help options with direct scheduling, but they are not pushed on you. This caters to individuals willing to dive in and those who want more guidance. Once your account email is verified, you will gain access to a dashboard that highlights your usage and relevant licenses.
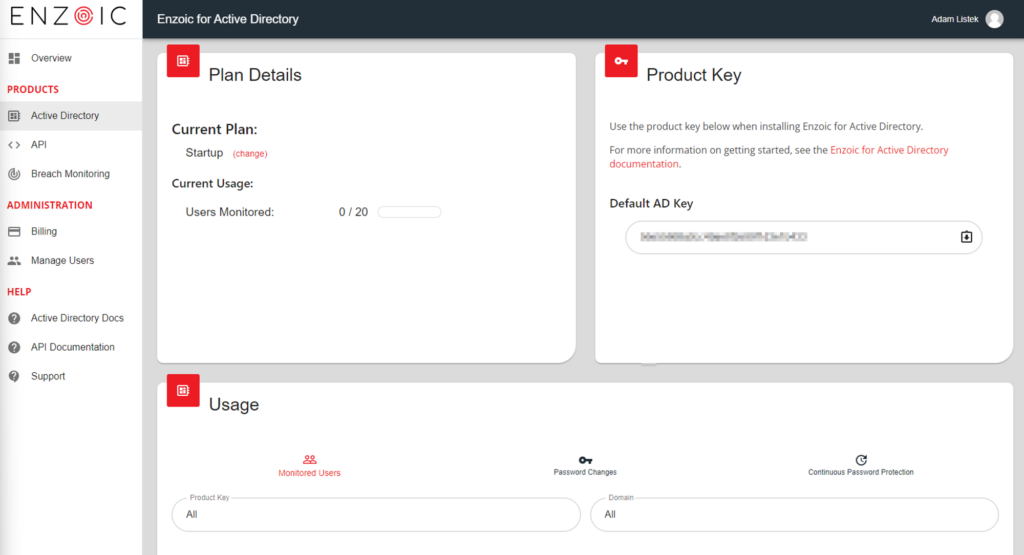
The Enzoic for Active Directory dashboard displays your product key, current plan, and usage details, such as the number of monitored users and the number of password change checks, and the accounts continuously monitored. But, it could be improved by adding a direct link to download the software packages. Currently, users must navigate to the documentation and download the file to install on their domain controller (DC).
Installing the Domain Controller Enzoic Agent
After launching either the downloaded executable (.exe) or MSI file, on the domain controller, a few screens will appear before a required restart of the domain controller. Subsequent application updates typically do not require a restart, but as a system administrator, you may need to plan ahead.
Installing this on read-only Domain Controllers is unnecessary, as password changes are handled on primary and secondary DCs. The Enzoic for Active Directory configuration is also stored within AD, so all settings are replicated to all DCs.
After the restart, the setup process will continue with the initial configuration upon login. Most configuration options will be covered during installation, allowing you to set reasonable starting values. I appreciate that most configurations are completed during installation, making deployment quick and simple.
The Enzoic for Active Directory application can be installed via automation through a YAML configuration file!
I’m not covering every option in the installation, but there are a few standout features. For instance, when specifying Monitored Entities, you can choose individual Users, Groups, or entire Organizational Units (OUs). But what I really appreciate is the option to disable Recursive Membership Checks. The only improvement I would like is this ability on a per-Group or per-OU basis.
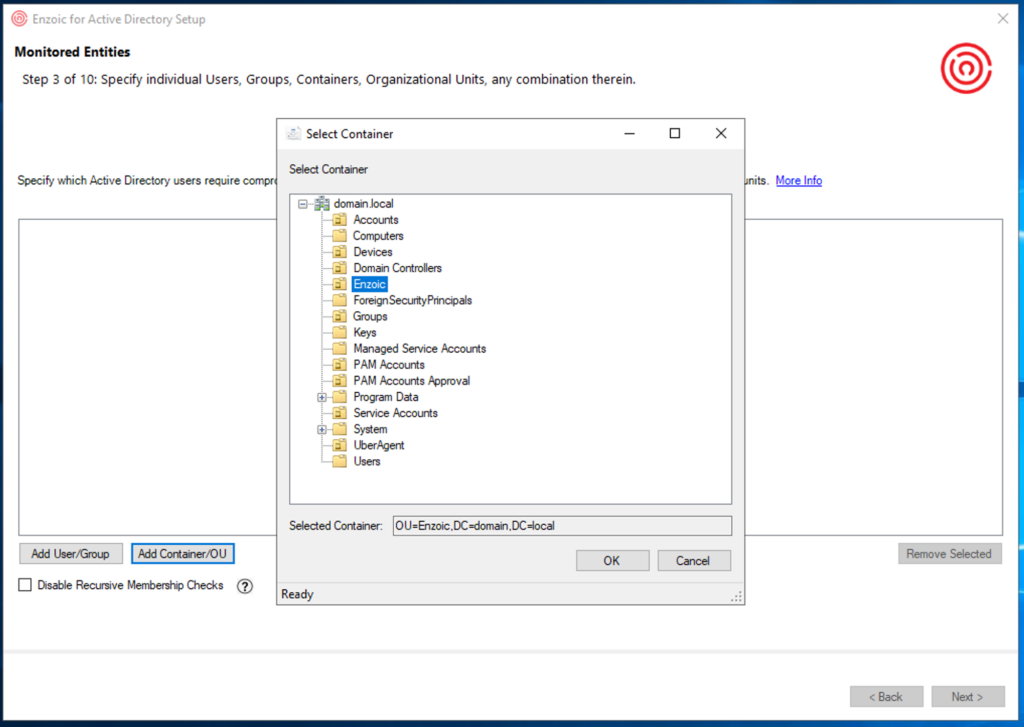
One significant advertised feature is the one-click NIST 800-63b compliance which configures Enzoic for Active Directory automatically for you. The following features must be enabled and configured to comply with NIST 800-63b.
- Continuous monitoring to detect when existing passwords become vulnerable.
- Common passwords that are found in cracking dictionaries.
- Fuzzy Matching for common patterns and substitutions.
- Custom dictionary for context-sensitive words that pertain to your business.
At the end of the setup process, you should test your connection to Enzoic and ensure that your configured settings are working as expected. This is a step that many other tools do not include, but I think it’s a great idea. Testing identifies issues early on and gives insight into the tool’s inner workings.
Behind the Scenes – How Does Enzoic for Active Directory Work?
You may wonder why you need to restart the domain controller. This is because Enzoic installs and registers a Microsoft standard password filter. The filter intercepts password requests to verify a password is not compromised and runs the configured Enzoic checks.
When dealing with a system that handles passwords, you may wonder how Enzoic securely handles them. Enzoic only transmits the first 10 characters of a password hash over a TLS 1.2, or greater, 256-bit encrypted connection to its servers, making the sent partial hashes impossible to reverse. All potential matches are then returned to the local domain controller, which compares the full password match to the returned matches locally.
Once the hashes have been returned, the Enzoic server memory is zeroed out, ensuring that Enzoic does not retain any partial password hash. If a returned hash matches, Enzoic alerts the administrator and user that a compromised password has been used.
If the user has a compromised password, it’s important that action is taken on the account. To that end, Enzoic can take the following actions:
- User Must Change Password on Next Login
- User Must Change Password on Next Login (Delayed)
- Disable Account
- Disable Account (Delayed)
- Notification Only
I do appreciate that you have the option to delay both a password change and disable the account. This gives flexibility to both users and administrators to ensure a smooth password change with minimal disruption.
Initial Steps with Enzoic for Active Directory
Once installed, launch the Enzoic for Active Directory dashboard application from the start menu. Upon the first launch, you will be presented with tiles displaying the current protection status. You will also have the option to do a scan of Active Directory. One improvement would be clicking on the information tiles to go directly to a report or setting.
This optional scan is equivalent to the Enzoic Active Directory Lite product, which performs a strict NTLM hash scan. But, it does not include features such as a custom local dictionary, fuzzy matching, or partial matches.
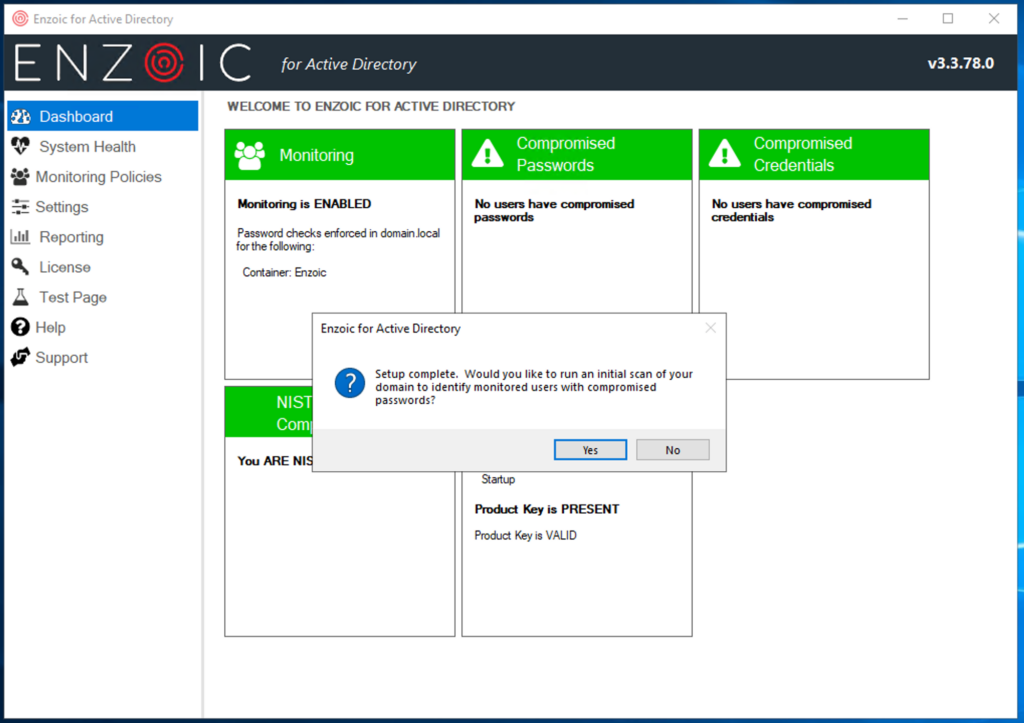
To fully use the password protection features, it is necessary to have all monitored accounts perform a password change. This will grant access to full user and credential monitoring and features like fuzzy matching. Unfortunately, this is not clearly explained when launching the initial scan, though the initial scan does offer protection with minimal disruption to end users.
When running a Monitored Users report within the Reporting section, you may immediately notice the limited nature of the monitoring. To understand why there is limited protection, users must rely on tooltips. It’s important to emphasize the need for monitored users to change their password after installation. This information should be front and center.
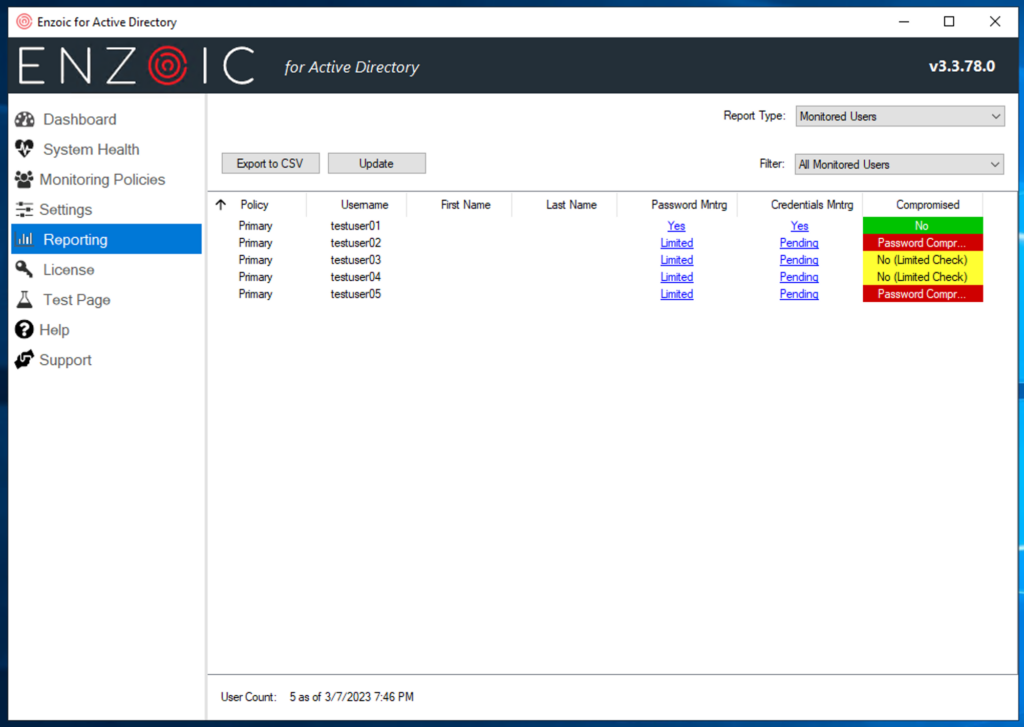
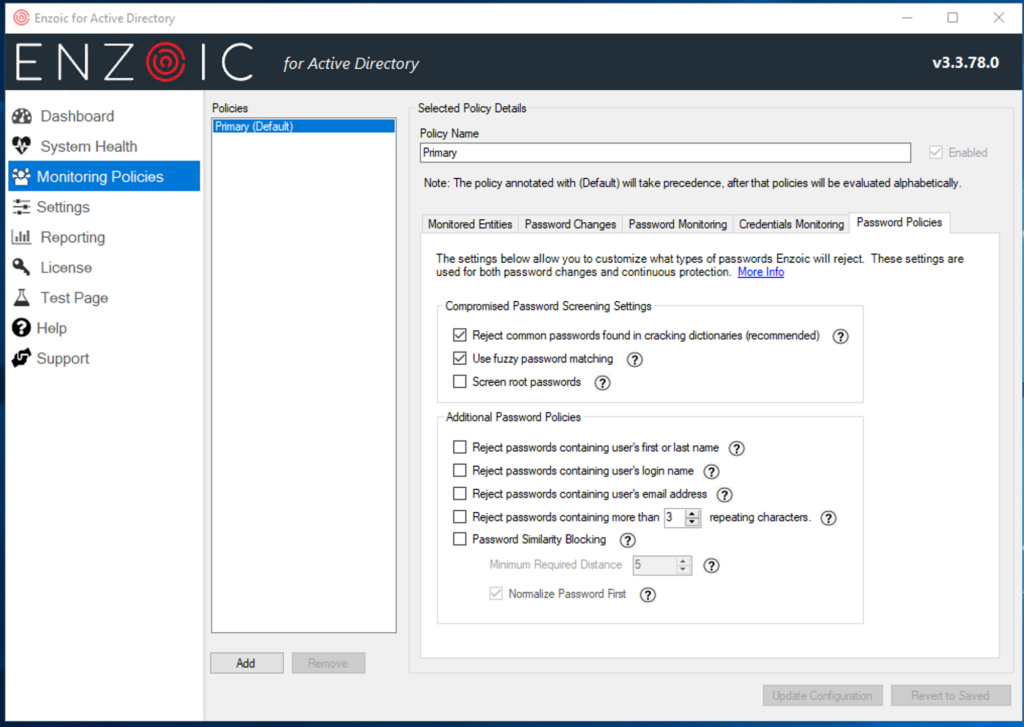
Before your users change their passwords, you may need to customize the Monitoring Policies. A nice feature is the ability to define multiple policies depending on the monitored entities. This type of control is excellent for users that need higher security settings where you may not need to impose a similar burden on all users.
Since a compromised monitored credential is more severe than a compromised password, Enzoic offers separate actions to take depending on the compromise. The passwords are all screened against a continuously updated database, a critical step for NIST compliance.
As noted in the below NIST recommendation, regular password changes are unnecessary and required in the case of a security breach. I appreciate that Enzoic helps to meet this requirement through its continuous monitoring against an updated breach database.
Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.
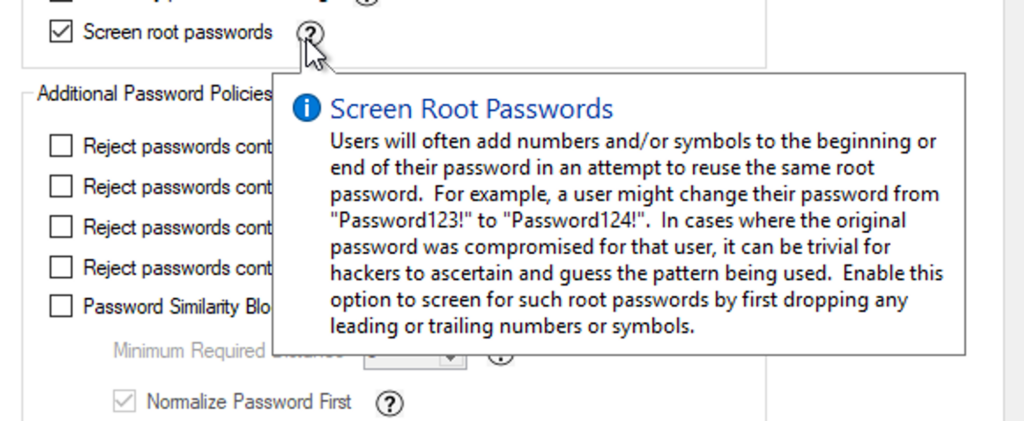
A feature of Enzoic that comes in handy for users that like to make simple modifications to passwords is the Screen Root Passwords option. Most users, at one time or another, for the sake of time have probably modified an easy-to-guess password in this way. To help keep their accounts safe, this monitor prevents those changes.
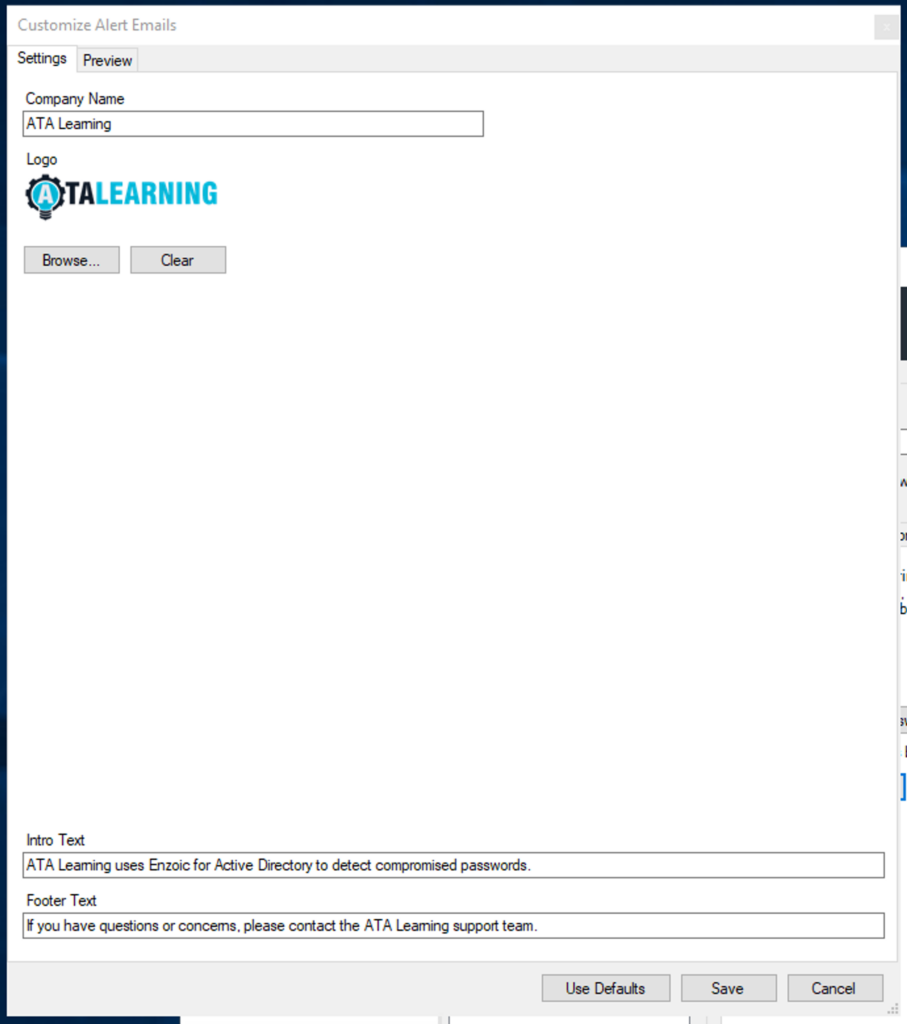
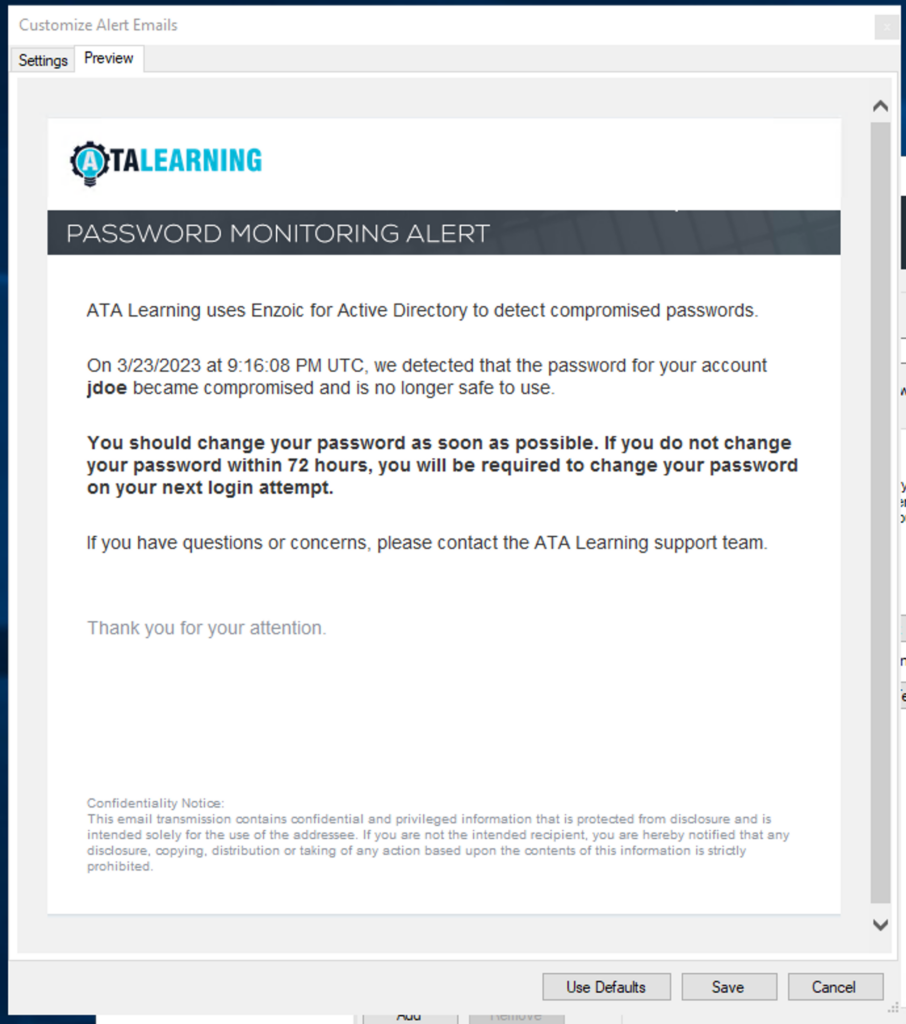
When a password is compromised, alerts should be sent to both administrators and users. Enzoic for Active Directory provides customization options for Password Monitoring and Credentials Monitoring, including email and password checking. While customization is limited, you can edit the company name, intro, and footer text and add a company logo to ensure a more trustworthy notification and provide further instructions relevant to your organization’s policy.
Integrating the Enzoic for Active Directory Windows Client
The Enzoic for Active Directory dashboard is helpful for system administrators. But how do you quickly notify a user that their password has been compromised? With the Enzoic for Active Directory Windows Client, if a user changes their password and it does not meet the required complexity or has been compromised, a message will be displayed to the user indicating the issue.
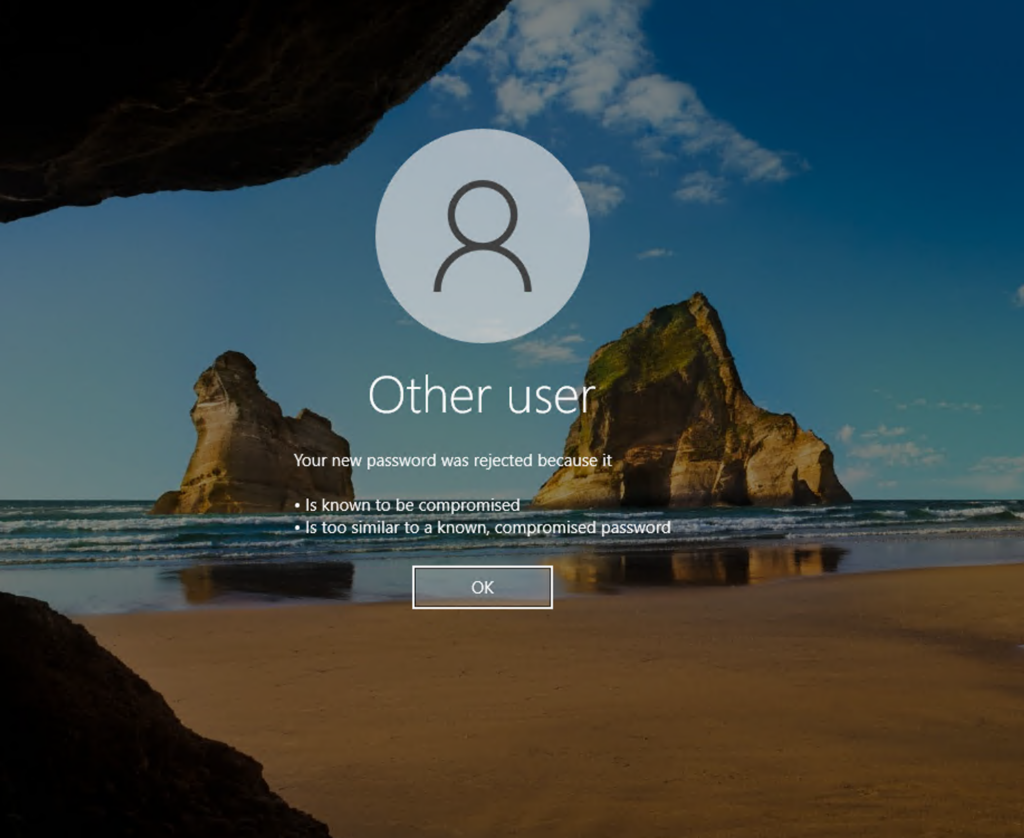
This client-side integration works hand-in-hand with the domain controller for monitored accounts to help users act quickly and ensure compliance. This works well, except for one limitation and one minor annoyance.
The Enzoic Client for Windows relies on the Microsoft credential provider framework, meaning only one provider can be active. This limits the availability of other authentication methods, such as Windows Hello for Business. Another minor annoyance is that you may need to enter your credentials twice when using a remote desktop protocol (RDP) session. This may be frustrating for technicians and remote workers, but I don’t consider it a dealbreaker.
The Enzoic for Active Directory Windows Client can be deployed via Group Policy for quick and easy deployments across your organization!
Pricing Plans Offered by Enzoic for Active Directory
Password and credential monitoring may be expensive, but depending on the size of your organization, that may not be the case. I believe that Enzoic offers a very reasonable pricing structure for many organizations.
The first 20 monitored users are free, which is a great way to try out and protect your most important accounts. For small organizations, such as many small businesses and non-profits, this is a perfect option for account protection. The total cost to protect 500 users with credential monitoring (Premium Plan) is $559 monthly.
| Users | Price | Total Protected Users |
|---|---|---|
| First 20 | Free | 20 |
| Next 80 | $160 ($2 per user) | 100 |
| Next 300 | $399 ($1.33 per user) | 400 |
Spending over $500 monthly to protect against customer data exposures or infrastructure compromises may be reasonable for mid-sized organizations. Small organizations can also benefit without a considerable cost, as the first 20 users are always free. Enzoic offers Enterprise plans for large organizations that may better fit their needs.
Enzoic for Active Directory: Recommended or Not?
After thoroughly testing and checking available options, I recommend Enzoic for Active Directory. While a few minor improvements could be made to the user interface and the limited nature of monitoring prior to a password change, the overall protection provided by the service makes up for these shortcomings.
Whether you are a large or small organization, protecting your users from compromised passwords and credentials is crucial in today’s increasing threats. Enzoic for Active Directory provides a quick, easy, and affordable solution to protecting your users and organization.




